
Most organizations have grown in-organically over the past few years with mergers and acquisitions where planning for data, lacked the focus. Moreover, there is no account of the growing private information that is collected or was collected from customers, employees and third parties.
Most of this personal information is vulnerable to threats and events of malicious theft, accidental disclosure, failure inappropriate usage, non-compliance with regulations. This increasingly is a concern to the regulators and organizations equally. The regulations are evolving and organizations with global operations must adopt globally to the highest regulatory requirements, from a region that can be leveraged as preparedness in other regions.
Protecting an organization’s reputation is the most significant risk management challenge today. Reputational risk is regarded as the greatest threat to a company's commercial value of the business.
The potential that negative publicity to an institution will cause a decline in the customer base, reduce revenue and lead to costly litigation.
Most of the privacy challenges can be addressed by Data Management and Governance divisions along with risk management functions. Privacy is defined in Generally Accepted Privacy Principles as “the rights and obligations of individuals and organizations with respect to the collection, use, retention, disclosure, and disposal of personal information”.
Private data can be a name, email address, Government identification number, a tax return to name a few.

Privacy is not only a requirement from GDPR but is also a major driver from an organization’s perspective of risk. Most of the personal information collected for years now is vulnerable to threats and events of malicious theft, accidental disclosure, failure inappropriate design, and usage. Today, protecting an organization’s reputation is the most significant risk management challenge. Negative publicity to a firm, will cause a decline in the customer base, reduce revenue and lead to costly litigation.

Most data privacy challenges can be addressed by Data Management and Governance divisions along with risk management functions. Privacy is defined in Generally Accepted Privacy Principles such as “the rights and obligations of individuals and organizations with respect to the collection, use, retention, disclosure, and disposal of personal information”. This can be a name, email address, Government identification number, a tax return to name a few.
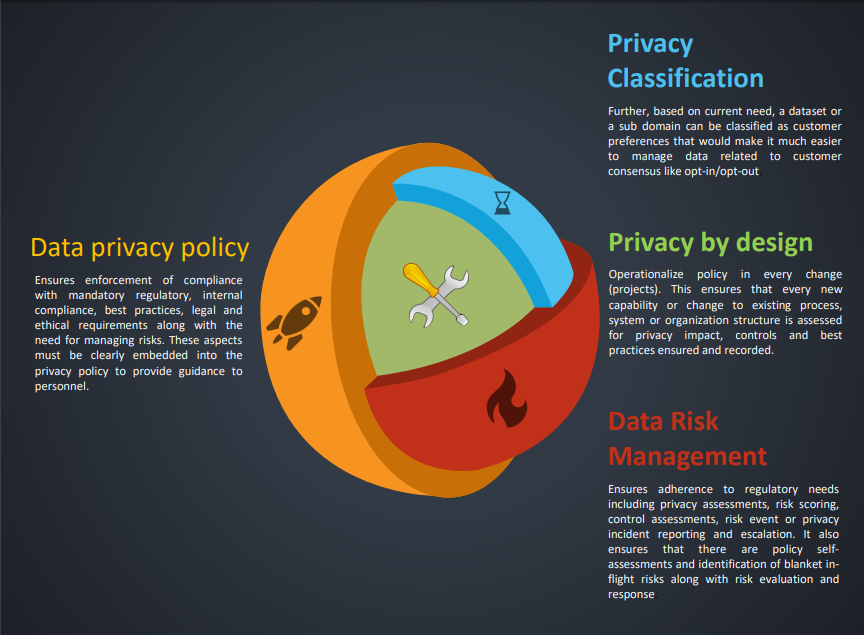
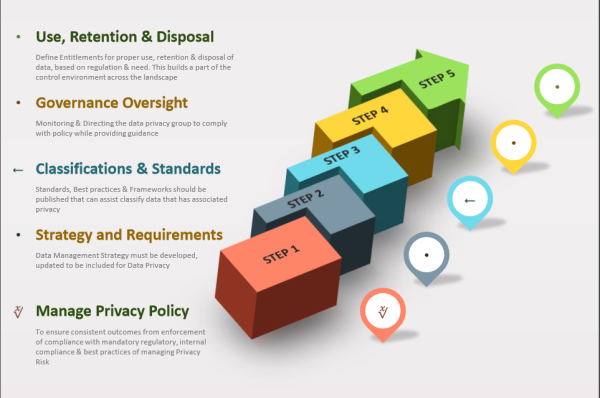
Organizations create data privacy policy to ensure enforcement of compliance with mandatory regulatory, internal compliance, best practices, legal and ethical requirements along with need for managing risk. The privacy statements also provide the need for capturing private information along with the rights that the customers enjoy in relation to the same. The guidance further is supported by the procedures...
Data Management Strategy must be developed, updated to include the Data Privacy management aspects. Data Management Strategy and Data Privacy Management must be aligned with Organizational objectives. In addition, describe the target structure and organizational structure for Data Privacy and Security Management.
Further, Roles and responsibilities are defined, communicated and enabled. The data governance division takes the responsibility of drafting policy, having reviews performed, publication and communication to the grassroots of enterprise. Further, Policy and standards are ensured to be reviewed and approved by risk function, senior executive governing bodies and governing councils.
The working groups are commissioned by Data Management to draft and publish the standards to classify data, in view of privacy and confidentiality.
Operational Risk Governance Structure and processes are in place and are operational. A risk assessment process is commissioned every year by second line of defense using the Risk Control Self-Assessment procedures, to identify new risks, understand the impact of events, and frequency of occurrence including the risk scores.
The organization describes the choices available to the individual and obtains implicit or explicit consent with respect to the collection, use, and disclosure of personal information.
It is to be ensured that the choices of individuals are captured with accuracy and the same is ensured with consistency wherever the consent, Opt-Ins and Opt-Outs are trickled along the data lifecycle.
The organization provides notice about its privacy policies and procedures and identifies the purposes for which personal information is collected, used, retained, and disclosed.
The privacy notice describes
Personal information collected
The purpose for which it will be used...
The organization collects personal information only for the purposes identified in the notice.
The Data Privacy Management must ensure alignment of the privacy policies with regulators across jurisdictions. This would necessitate that Cross-organizational enterprise data governance is aligned with Compliance and Legal functions to ensure registration of the organization with the...
Data Owners are accountable while data stewards are responsible to classify the data elements, defining entitlements, any associated distribution rules and defining data to process/system/people mapping.
Data lifecycle management strategy must be defined and endorsed by relevant stakeholders. Data lifecycle management roadmap must be developed and implemented. Storage governance structure, archival procedures, data transfer and Decay processes and procedures should be operational.
When individuals request access to their personal information, the most current and accurate information should be provided on authorization from data owner. Any further requests on maintenance or updation of existing records will be taken through the procedures to update personal information. While the same needs to be updated in golden sources, systems of references wherever the same data element exists.
Any data that is enhanced or transformed outside the organization, will be the responsibility of the organization performing the transformation. The data quality function ensures that data that is transferred to third party is accurate, complete, consistent, relevant and valid. The profile of data must be stored in the metadata repository by the profiling group while the Data Quality rules should be defined by the data owners and SMEs...
Every organization protects personal information against un-authorized access (both physical and logical). Privacy policies adequately address security measures to safeguard the privacy of personal information whether in electronic, paper, or other forms.
Security measures are consistent with the sensitivity of the personal information. Most often, the Data Privacy and security function calls for the creation of a communication and training program. Further, it must describe the need for an education and training program to ensure stakeholder understanding, buy-in, and compliance with the data privacy and security program.
Content Governance ensures that data Classifications including Data management characteristics, Data security, and privacy classification are established.
Stewardship and program governance ensure that privacy by design is embraced.
The controls for security for private data are established at a data service level wherever applicable rather than at an application level.
The divisional and governance forums ensure that the guidelines for data controls are placed for new changes or changes to existing capabilities. Once the Privacy Impact Assessments are performed, the gaps are analyzed and a program focusing on establishing a control environment for such data is commissioned
The level of controls includes administrative, technical and physical controls to secure sensitive data. The data quality function ensures that adequate integrity controls are in place to maintain the data while data privacy and security ensures that modification is being performed by designated roles. The Data governance function must be aligned with information security policy.